ISCTFwp
WriteUp
Misc
小蓝鲨的签到01
扫码即得flag
小蓝鲨的签到02
strings命令查找即得flag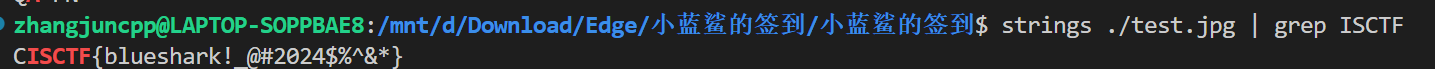
游园地1
开盒题都在武汉江汉路附近,武带人狂喜
谷歌搜图,https://news.qq.com/rain/a/20231023A06PFW00 就有个极其相似的地方,查得此地为武汉中山公园。
故flag为ISCTF{湖北省_武汉市_江汉区_中山公园}
游园地2
继续谷歌搜图,https://www.taptap.cn/moment/592096524821860169 有个几乎一模一样的图,看评论区知道这个是【充能国安路】的原型。
搜充能国安路,https://blog.l3zc.com/2023/08/wuhan-trip/#%E5%85%85%E8%83%BD%E5%9B%BD%E5%AE%89%E8%B7%AF 这里搞出了游戏名和原型街道,高德一搜竟然还是武汉江汉区的地方(你们二次元是有多喜欢江汉路啊)
得到flag:ISCTF{湖北省_武汉市_江汉区_鸣笛1988商业街_恋爱绮谭}
Reverse
EzRe
动调发现核心加密逻辑在这里: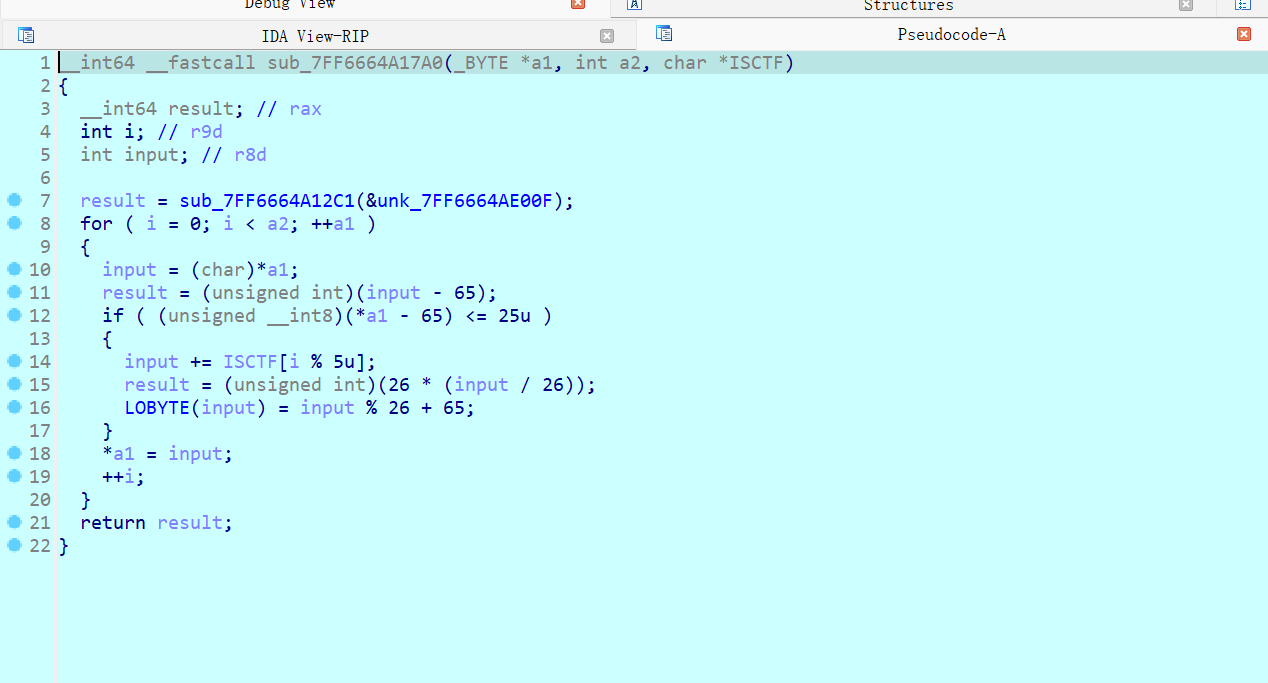
又知道加密后的字符串QKEMK{7JB5_i5_W3SllD_3z_W3},直接解密即可:
1 | |
你知道.elf文件嘛
拖进IDA发现竟然全是LOAD段,无从下手,干脆先随便执行一下算了……执行后发现只要按要求输入base64码表即可get flag。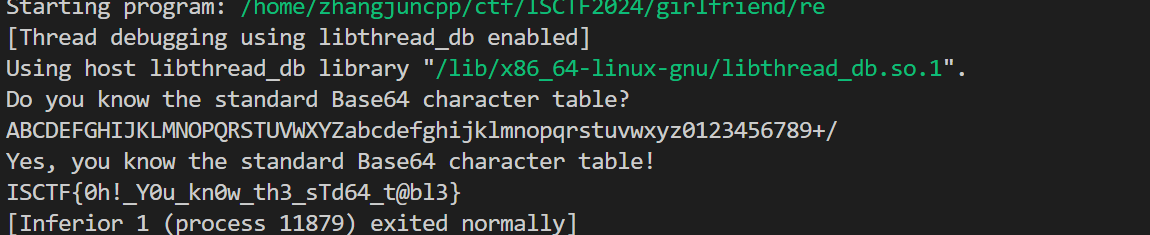
《回忆安魂曲》–第二章:当记忆被割裂
拖进IDA尝试F5反编译,几乎所有函数都飘红冒出JUMPOUT,显然是花指令。观察发现程序实际上是把地址加载到栈上,再利用复杂的指令进行jmp rax跳转。尝试nop+patch恢复似乎没什么卵用,毕竟栈帧调用及其费解,难以恢复正常。
做这题的是pwn手,于是在IDA调试没出什么成果的情况下果断采用pwndbg调试,终于缕清了程序逻辑: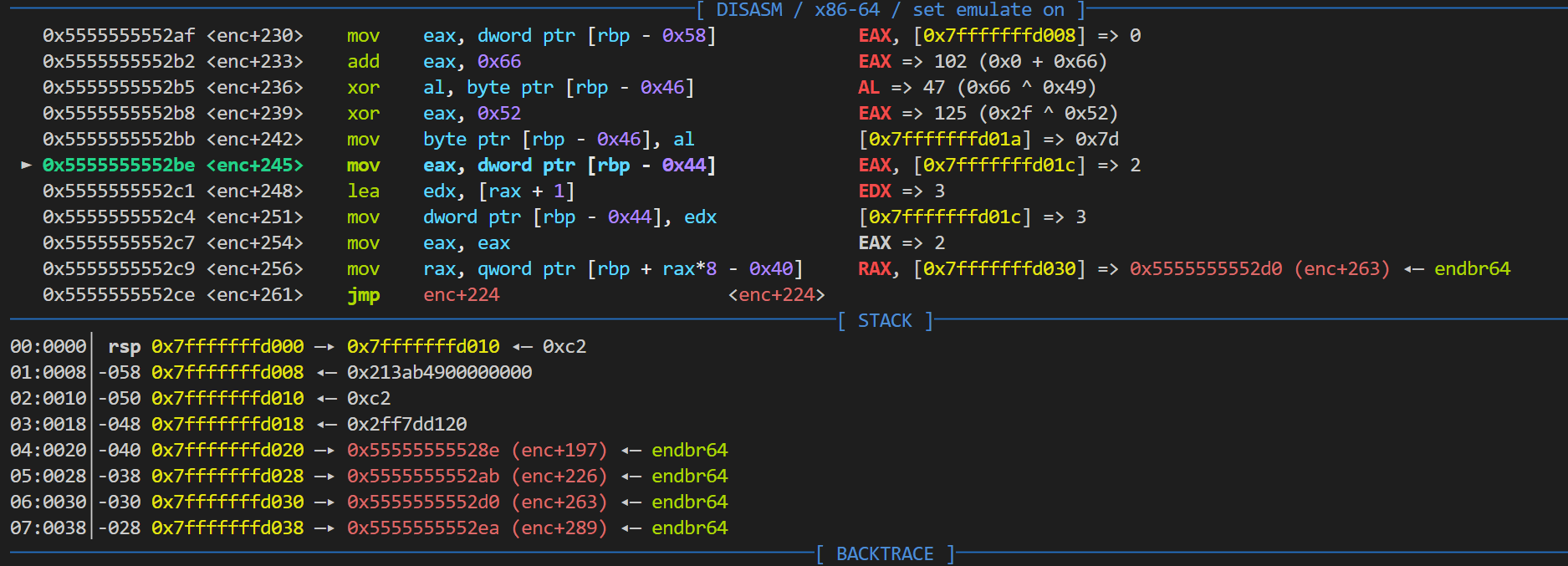
发现数据段上有ans和key,基本上就是answer和key了。利用pwndbg逐步审计汇编代码,发现程序的加密函数enc逻辑如下:
- 设当前字符为
now,索引为i - now ^= (0x66+i)
- now ^= 0x52
- now += 6
- now ^= (key[i]+i)
缕清了加密逻辑、找到了密文和密钥之后,解密就不难了。
1 | |
《回忆安魂曲》–第三章:逃不出的黑墙
迷宫饭题,先从IDA中把迷宫提出来,再让AI写个BFS脚本查路径就行了。
1 | |
Pwn
Netcat
nc就给flag,甚至不用cat。哪怕是签到题也显得过于简单了。
girlfriend
普通的ret2text,给了后门函数,数组索引越界。需要注意的是溢出会覆盖i,i的值必须精心布置才行;另外要ret到那个lea指令处,防止栈不对齐导致错误。
1 | |
ret2orw
板子题,开了沙箱禁用execve,用ret2libc同款手法打orw即可。
1 | |
ez_game
普通的打随机数,好处是可以栈溢出控制seed,不会有远程和本地时间差导致的错误。
1 | |
0verf10w
非常恶心,格串+canary绕过+ret2libc+栈迁移。首先利用格串漏洞把程序基地址、libc基地址、栈地址、canary值全部leak出来,此时main函数的canary已损坏,不过我们一会儿可以打栈迁移绕过检查,不必理会;接下来利用vuln函数里的off-by-one,覆盖rbp指向的位置的低字节,实现栈迁移,这样就可以劫持控制流重启main了。接下来就常规ret2libc打通即可。
1 | |
orange
ByteCTF2024原题,只不过去了符号表、加了花指令。nop掉花指令后分析,发现没有free,考虑house of orange攻击,利用unsorted bin泄露libc和堆地址后打IO即可。
1 | |
小蓝鲨stack
ret2libc板子。注意printf需要栈对齐,也包括重启main后的printf,需要用ret对齐。
1 | |
syscall
给了3次syscall的机会,利用shmget+shmatleak libc,拿出/bin/sh地址,再execve即可。
1 | |